This article outlines privacy issues with WiFi enabled smartphones and my tracking approach using a few lines of code. Using a $2 chinese wireless USB adapter, an old Raspberry Pi B and Scapy I was able to track peoples habits and visualize their homes location in realtime.
Disclaimer: In most (European) countries this proceeding will likely violate the data privacy act and might be illegal. I wont disclose any raw data and all gathered information have been either anonymized or deleted.
Getting started
First of all we need a WiFi adapter which supports monitoring mode. Using this mode we can passively listen for WiFi signals around. Additionally we need a Linux System running aircrack-ng, Python3, scapy, manuf and a MySQL Database server.
What data are we going to collect?
Every wireless device which is not associated to a wireless network will regularly send out probe requests. Those requests are used to identify known networks. They always contain the devices MAC address and sometimes a list of wireless network names (SSIDs) the device is looking for.
As MAC addresses are (pretty) unique we can easily start recording the MAC addresses of devices around us over a long time. Assuming that most people own a personal used smartphone we can infer that there is a single person behind every MAC address
Start monitoring
Using my open source tools available on GitHub we can easily monitor the devices around us, resolve their manufacturer and store the time spans they were near to us. Furthermore all SSIDs a device probed for will be stored as well.
The location
All tests have been performed at a village near to a bus stop. As the bus connections are bad they are mostly used by pupils to go to school. This makes the data much more attractive as most of them will own a smartphone and we might be able to reconstruct their timetables.
First results
After running the tool for a few weeks, I collected 920 MAC addresses which were seen at least three times and 954 SSIDs from wireless probes.
SSIDs
As the raw data about devices is nearly useless at this point, we will start with a survey around the probed SSIDs. Of course there are a lot of generic SSIDs like dlink but also many unique SSIDs which can be easily mapped to locations.
Home Access Points
For technical reasons it makes sense to ship access points for home usage with a default, non-generic SSIDs. This ensures that a device only tries to connect to the the wireless network at home and doesn’t ask the user for the password of a totally different network which just shares the same, generic SSID.
However this makes users easily trackable as the SSID will be only probed by a small set of devices. Furthermore the SSID can be used to check for the home location using publicly available wardriving maps like wigle.net.
Holiday Locations, Schools and Shopping Places
At this point we might already know the users home location but can we find more about their habits? Yes we can!
Apart from home networks, I also collected many SSIDs of hotels which allow us to find out more about the last holiday trip. Also many schools offer wireless networks for their students and thus we become able to determine that a family which owns a wireless network has at least one child visiting school X.
As super markets also offer free WiFi for their customers we can also see the preferred shopping place of a person and map which area of a city purchases at a specific shop
Smart City and IoT
Enough of these buzzwords. I also collected SSIDs from devices which are obviously belonging to various companies like parcel delivery services or the public transport.
DPD seems to have scanners probing for the network DPD_HALLE and the local bus company seems to own the network ITCS (Intermodal Transport Control System). Now you can proof if a bus was late or the delivery vehicle skipped your place. Furthermore those SSIDs reveal interesting targets for some attacks on wireless networks.
MAC Randomization
At least iOS devices and I think a few Android devices as well implement a MAC address randomization to protect the users privacy. However this randomization is not as good as advertised.
In Germany we have the initiative Freifunk which offers free wireless networks and supports private persons to protect themselves from consequences of the illegal use of their open wireless network. Many devices connect to this SSID and as the MAC address is only randomized while the device is not associated to a network, it is enough to place an Access Point called Freifunk to get the real MAC address.
Many Android devices are crap!
Did you wonder why I got so many SSIDs? Me too! Normally a device sends only probe requests for hidden SSIDs but many Android devices probe for all SSIDs they know. This results in a bunch of emitted SSIDs and makes tracking much easier.
Beginning the fun
As the region around the bus stop is relatively small, I started to do some wardriving in the evening when most people are at home. Using kismet I mapped all SSIDs and the MAC addresses of the connected devices according to my GPS position. This data was used to find the home location of a device
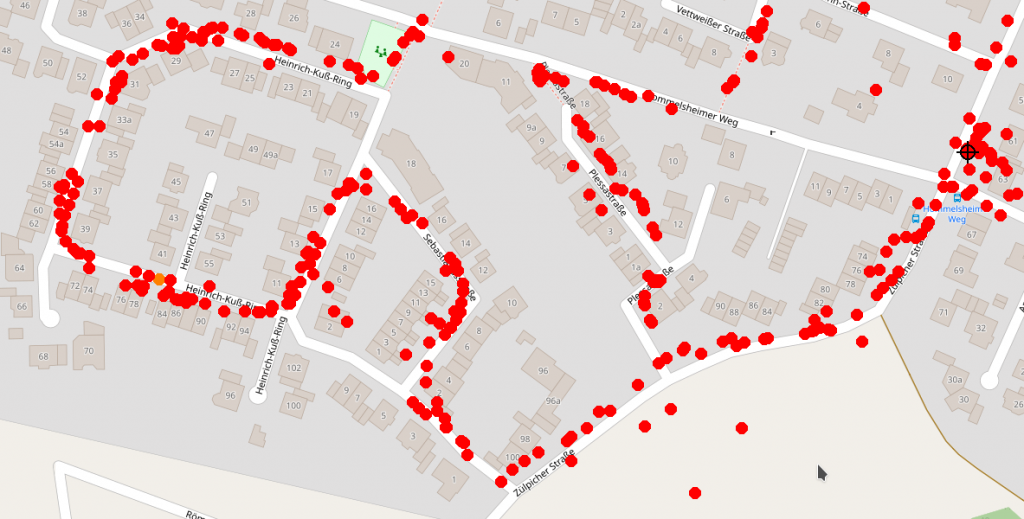
This allows us to grab a random device from my database and see it’s home location. But I wanted to do more. For this case study I chose a SSID of a School in Düren. I had seen four devices probing for this SSID and found two of them connected to a wireless network. We will call them 103 and 177.
Timetables
First of all we will try to find out something about the students timetables. So I fetched the session log for all four devices. All dates have been converted to local time.
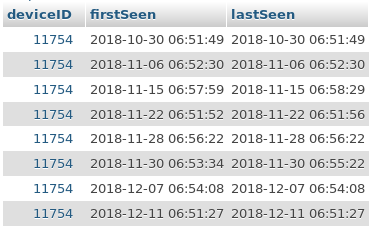
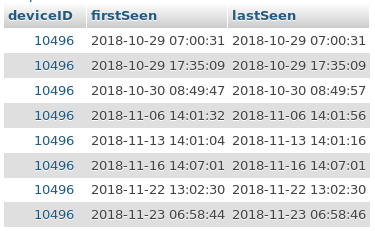
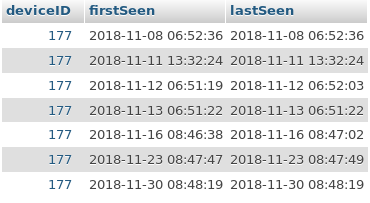
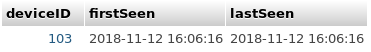
It is obvious that most students depart early in the morning and take either the bus at 6:52am or 6:57am. There are only two students (177 and 10496) departing regularly at 8:47am which means that they start with school after the first break. As I’m a former student of this school I know, that this normally only applies for higher grades.
It also becomes abvious that my antenna should be moved much closer to the bus stop to get more reliable results. Anyways this data might reveal more interesting information like the position at the bus stop where the person normally stands.
Device 103 (Huawei)
Now it’s time to find out as much as possible about the device, it’s network and family members.
Using my wardriving data I found out, that device 103 was connected to a wireless network I don’t want to reveal the ESSID of as it is not unique. However you can see it’s position on the map. The red dot shows the networks position, the cross shows my antennas position.
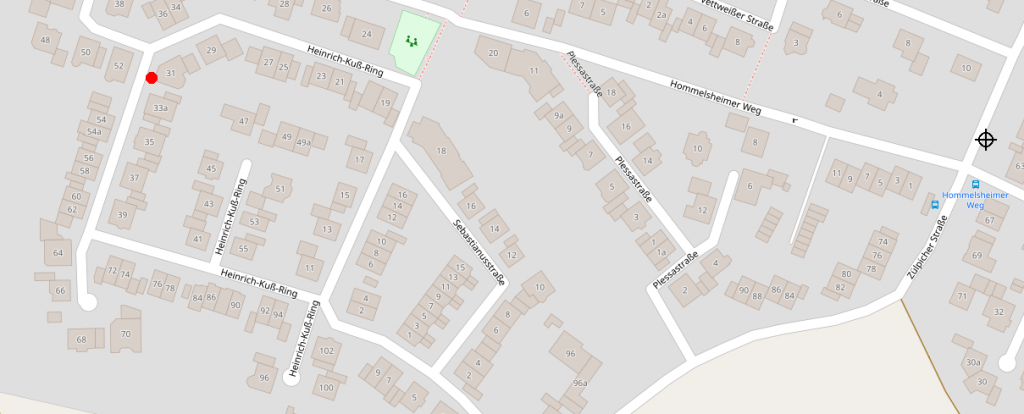
Now checking out the other connected devices I found out that I saw a total of 10 devices connected to the specific network. Three more of them (two Apple devices and a SONY Device) sent probes I collected as well. Again we will take a closer look for each device ID.
105 (Apple)
This device has been seen one time and dind’t send any interesting probes. It has been recorded by my Freifunk honeypot. As I din’t see the device more often I except the owner normally moving by car.
1760 (Apple)
This device has been seen multiple times and dind’t send any interesting probes. It has been recorded by my Freifunk honeypot.
6842 (SONY)
This device has been seen several times. It probed for a network SSID which is according to wigle.net located in Mönchengladbach.
177 (SAMSUNG)
Now taking a look at the other device I initially put in relation to the schools network. Again I had success to locate the network and again it doesn’t have a generic name I could reveal. It seems to be a Dualband Access Point so I have to look for two wireless networks to find connected devices.
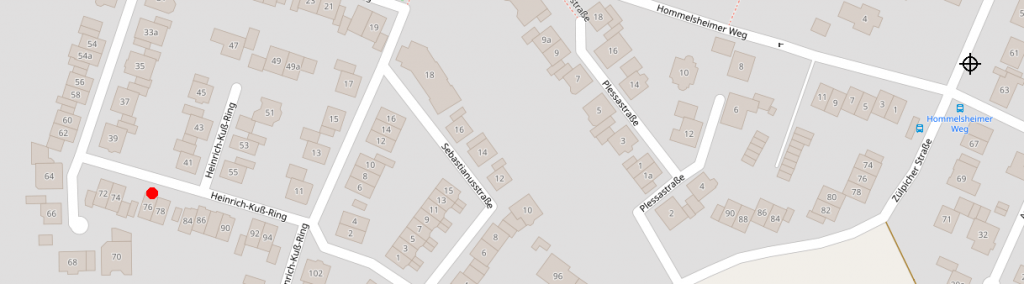
I found a total of 7 devices connected to the network. But no more devices sent probes I recorded.
Conclusion
Spending more time with this project I could build an automated analysis tool and an integration for the wigle API to track devices and thus families in a bigger scale. But I don’t want to continue this project as it has shown how much sensitive data we reveal every day by using our smartphone.
Random MAC addresses aren’t a solution and by using more devices capturing wireless probes we could improve the tracking.
Never do sensitive things using wireless networks. In case you don’t want to be tracked, consider to turn off WiFi on your smartphone or better leave your phone at home.
[…] Lustig: Jemand hatte wohl am Wochenende die selbe Idee […]
Lustig, wir hatten wohl die letzten Tage die selbe Beschäftigung 😉 https://blog.rolandmoriz.de/2019/01/08/eine-flasche-metadaten-2-wifi-probes/